Creating Gateway to Gateway VPN using Cisco RV042 Routers. Please check your tunnel endpoint (gateway) setting' followed by 'Dynamic VPN client in Main Mode is only supported for Microsoft VPN client, please use Aggressive mode instead.' I had been fiddling with the 'VPN - VPN Client Access' screen of the RV042, but now have read that this data only applies to users using the Linksys QuickVPN client. Hi, I'm new to VPN. I configured a Client to Gateway vpn tunnel in RV042. I can connect to it successfully using QuickVPN. I have some questions about the connection: In the VPN summary page, the status of the tunnel is 'Waiting for Connection' even though vpn connection has been established usi. VPN rv042 Client to Gateway Hola a todos y de antemano gracias por su tiempo. Les comento que recientemente compre un equipo Cisco RV042 y necesito ponerlo en la empresa para que los usuarios se conecten por VPN y poder usar los recursos de la misma y tambien acceder a escritorio remoto.
Objective
A Virtual Private Network (VPN) is used to form a secure connection between two endpoints over a public or shared Internet, through what is called a VPN tunnel. More specifically, a gateway-to-gateway VPN connection allows for two routers to securely connect to each other and for a client on one end to logically appear as if they are a part of the network on the other end. This enables data and resources to be shared more easily and securely over the Internet.
Configuration must be done on both routers to enable a gateway-to-gateway VPN. The configurations done in the Local Group Setup and Remote Group Setup sections should be reversed between the two routers so that the local group of one is the remote group of the other.
The objective of this document is to explain how to configure Gateway-to-Gateway VPN on RV016, RV042, RV042G and RV082 VPN Series Routers.
Applicable Devices
• RV016
• RV042
• RV042G
• RV082
Software Version
• v4.2.2.08
Configure Gateway to Gateway VPN
Step 1. Log in to the Router Configuration Utility and choose VPN > Gateway to Gateway. The Gateway to Gateway page opens:
To configure gateway to gateway VPN the following features need to be configured:
1. Add a New Tunnel
2. Local Group Setup
Cisco Rv042 Vpn Setup Client To Gateway Password
3. Remote Group Setup
4. IPSec Setup
Add a New Tunnel
Tunnel No. is a read only field that displays the current tunnel that is going to be created.
Step 1. Enter a name for the VPN tunnel in the Tunnel Name field. It does not have to match the name used at the other end of the tunnel.
Step 2. From the Interface drop-down list choose the Wide Area Network (WAN) port to use for the tunnel.
• WAN1 — The dedicated WAN port of the RV0XX series VPN routers.
• WAN2 — The WAN2/DMZ port of the RV0XX Series VPN routers. Only displays in the drop-down menu if it has been configured as a WAN and not a Demilitarize Zone (DMZ) port.
Step 3. (Optional) To enable the VPN, check the check box in the Enable field. The VPN is enabled by default.
Local Group Setup
Note: The configuration for the local group setup on one router should be the same as the configuration for the remote group setup on the other router.
Step 1. Choose the appropriate router identification method to establish a VPN tunnel from the Local Security Gateway Type drop-down list.
• IP Only — The local router (this router) is recognized by a static IP address. You can only choose this option if the router has a static WAN IP. The static WAN IP address appears automatically in the IP Address field.
• IP + Domain Name (FQDN) Authentication — Access to the tunnel is possible through a static IP address and a registered domain. If you choose this option, enter the name of the registered domain in the Domain Name field. The static WAN IP address appears automatically in the IP Address field.
• IP + E-mail Addr.(USER FQDN) Authentication — Access to the tunnel is possible through a static IP address and an email address. If you choose this option, enter the email address in the Email Address field. The static WAN IP address appears automatically in the IP Address field.
• Dynamic IP + Domain Name (FQDN) Authentication — Access to the tunnel is possible through a dynamic IP address and a registered domain. If you choose this option, enter the name of the registered domain in the Domain Name field.
• Dynamic IP + Email Addr.(USER FQDN) Authentication — Access to the tunnel is possible through a dynamic IP address and an email address. If you choose this option, enter the email address in the Email Address field.
Step 2. Choose the appropriate local LAN user or group of users who can access the VPN tunnel from the Local Security Group drop-down list. The default is Subnet.
• IP — Only one LAN device can access the VPN tunnel. If you choose this option, enter the IP address of the LAN device in the IP Address field.
• Subnet — All LAN devices on a specific subnet can access the tunnel. If you choose this option, enter the subnetwork IP address and subnet mask of the LAN devices in the IP Address and Subnet Mask field respectively. The default mask is 255.255.255.0.
• IP Range — A range of LAN devices can access the tunnel. If you choose this option, enter the starting and ending IP address in the Begin IP and End IP fields respectively.
Step 3. Click Save to save the settings.

Remote Group Setup
Note: The configuration for the remote group setup on one router should be the same as the configuration for the local group setup on the other router.
Step 1. From the Remote Security Gateway Type drop-down list, choose the method to identify the remote router to establish the VPN tunnel.
• IP Only — Access to the tunnel is possible through a static WAN IP. If you know the IP address of the remote router, choose IP address from the drop-down list directly below the Remote Security Gateway Type field and enter the IP address. Choose IP by DNS Resolved if you do not know the IP address but know the domain name and enter the domain name of the router in the IP by DNS Resolved field.
• IP + Domain Name (FQDN) Authentication — Access to the tunnel is possible through a static IP address and a registered domain for the router. If you know the IP address of the remote router, choose IP address on the drop-down list directly below the Remote Security Gateway Type field and enter the address. Choose IP by DNS Resolved if you do not know the IP address but know the domain name and enter the domain name of the router in the IP by DNS Resolved field. Enter the domain name of the router in the Domain Name field regardless of which method you choose to identify it by.
• IP + Email Addr.(USER FQDN) Authentication — Access to the tunnel is possible through a static IP address and an email address. If you know the IP address of the remote router, choose IP address on the drop-down list directly below Remote Security Gateway Type field and enter the address. Choose IP by DNS Resolved if you do not know the IP address but know the domain name and enter the domain name of the router in the IP by DNS Resolved field. Enter the e-mail Address in the Email Address field.
• Dynamic IP + Domain Name (FQDN) Authentication — Access to the tunnel is possible through a dynamic IP address and a registered domain. If you choose this option, enter the name of the registered domain in the Domain Name field.
• Dynamic IP + Email Addr.(USER FQDN) Authentication — Access to the tunnel is possible through a dynamic IP address and an email address. If you choose this option, enter the Email Address in the Email Address field.
Step 2. Choose the appropriate remote LAN user or group of users who can access the VPN tunnel from the Remote Security Group Type drop-down list.
• IP — Only one specific LAN device can access to the tunnel. If you choose this option, enter the IP address of the LAN device in the IP Address field.
• Subnet — All LAN devices on a specific subnet can access to the tunnel. If you choose this option, enter the subnetwork IP address and subnet mask of the LAN devices in the IP Address and Subnet Mask field respectively.
• IP Range — A range of LAN devices can access to the tunnel. If you choose this option, enter the starting and ending IP address in the Begin IP and End IP fields respectively.
Note: The two routers at the ends of the tunnel cannot be on the same subnet.
Step 3. Click Save to save the settings.
IPSec Setup
Internet Protocol Security (IPSec) is an internet layer security protocol which provides end-to-end security through authentication and encryption during any communication session.
Note: Both ends of the VPN need to have the same methods of encryption, decryption, and authentication to work properly. Enter the same IPSec Setup settings for both routers.
Step 1. Choose the appropriate mode of key management to ensure security from the Keying Mode drop-down list. The default mode is IKE with Preshared key.
• Manual — A custom security mode to generate a new security key by yourself and no negotiation with the key. It is the best to use during troubleshooting and in a small static environment.
• IKE with Preshared key — Internet Key Exchange (IKE) protocol is used to automatically generate and exchange a preshared key to establish authenticate communication for the tunnel.
IPSec Setup for Manual Keying Mode
Step 1. Enter the unique hexadecimal value for incoming Security Parameter Index (SPI) in the Incoming SPI field. SPI is carried in the Encapsulating Security Payload Protocol (ESP) header and determines the protection for the incoming packet. You can enter a value from 100 to ffffffff. The incoming SPI of the local router needs to match with the outgoing SPI of the remote router.
Step 2. Enter the unique hexadecimal value for outgoing Security Parameter Index (SPI) in the Outgoing SPI field. You can enter a value from 100 to ffffffff. The outgoing SPI of the remote router need to match with the incoming SPI of the local router.
Note: No two tunnels can have the same SPI.
Step 3. Choose the appropriate encryption method for the data from the Encryption drop-down list. The recommended encryption is 3DES. The VPN tunnel needs to use the same encryption method on both ends.
• DES — Data Encryption Standard (DES) uses a 56-bit key size for data encryption. DES is outdated and should be only used if one endpoint only supports DES.
• 3DES — Triple Data Encryption Standard (3DES) is a 168 bit, simple encryption method. 3DES encrypts the data three times, which provides more security then DES.
Step 4. Choose the appropriate authentication method for the data from the Authentication drop-down list. The recommended authentication is SHA1 as it is more secure than MD5. The VPN tunnel needs to use the same authentication method for both ends.
• MD5 — Message Digest Algorithm-5 (MD5) is a 128 bit hash function which provides protection to the data from malicious attack by the checksum calculation.
• SHA1 — Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
Step 5. Enter the key to encrypt and decrypt data in the Encryption Key field. If you choose DES as encryption method in Step 3, enter a 16 digit hexadecimal value. If you choose 3DES as encryption method in Step 3, enter a 40 digit hexadecimal value.
Step 6. Enter a pre-shared key to authenticate the traffic in Authentication Key field. If you choose MD5 as authentication method in step 4, enter 32 digit hexadecimal value. If you choose SHA1 as authentication method in Step 4, enter 40 digit hexadecimal value. If you do not add enough digits, zeroes will be appended to the end until there are enough digits. The VPN tunnel needs to use the same pre-shared key for both of the ends.
Step 7. Click Save to save the settings.
IKE with Preshared Key Mode Configuration
Step 1. Choose the appropriate Phase 1 DH Group from the Phase 1 DH Group drop-down list. Phase 1 is used to establish the simplex, logical security association (SA) between the two ends of the tunnel to support secure authenticate communication. Diffie-Hellman (DH) is a cryptographic key exchange protocol which is used to determine the strength of the key during Phase 1 and it also shares the secret key to authenticate the communication.
• Group 1 - 768 bit —The lowest strength key and the most insecure authentication group but takes the least amount of time to compute the IKE keys. This option is preferred if the speed of the network is low.
• Group 2 - 1024 bit — A higher strength key and more secure authentication group than group 1 but it takes more time to compute the IKE keys.
• Group 5 - 1536 bit — The highest strength key and the most secure authentication group. It needs more time to compute the IKE keys. It is preferred if the speed of the network is high.
Step 2. Choose the appropriate Phase 1 Encryption to encrypt the key from the Phase 1 Encryption drop-down list. AES-128, AES-192, or AES-256 are recommended. The VPN tunnel needs to use the same encryption method for both of its ends.
• DES — Data Encryption Standard (DES) uses a 56-bit key size for data encryption. DES is outdated and should be only used if one endpoint only supports DES.
• 3DES — Triple Data Encryption Standard (3DES) is a 168 bit, simple encryption method. 3DES encrypts the data three times, which provides more security then DES.
• AES-128 — Advanced Encryption Standard (AES) is 128 bit encryption method which transforms the plain text into cipher text through 10 cycles repetitions.
• AES-192 — Advanced Encryption Standard (AES) is 192 bit encryption method which transforms the plain text into cipher text through 12 cycles repetitions. AES-192 is more secure than AES-128.
• AES-256 — Advanced Encryption Standard (AES) is 256 bit encryption method which transforms the plain text into cipher text through 14 cycles repetitions. AES-256 is the most secure encryption method.
Step 3. Choose the appropriate Phase 1 authentication method from the Phase 1 Authentication drop-down list. The VPN tunnel needs to use the same authentication method for both of its ends. SHA1 is recommended.
• MD5 — Message Digest Algorithm-5 (MD5) is a 128 bit hash function which provide protection to the data from malicious attack by the checksum calculation.
• SHA1 — Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
Step 4. Enter the amount of time in seconds that the Phase 1 keys are valid and the VPN tunnel remains active in the Phase 1 SA Life Time field.
Step 5. Check the Perfect Forward Secrecy check box to provide more protection to the keys. This option allows the router to generate a new key if any key is compromised. The encrypted data is only compromised through the compromised key. This is a recommended action as it provides more security.
Step 6. Choose the appropriate Phase 2 DH Group from the Phase 2 DH Group drop-down list. Phase 2 uses security association and is used to determine the security of the data packet as it passes through the two end points.
• Group 1 - 768 bit —The lowest strength key and the most insecure authentication group, but takes the least amount of time to compute the IKE keys. This option is preferred if the speed of the network is low.
• Group 2 - 1024 bit — A higher strength key and more secure authentication group than group 1, but takes more time to compute the IKE keys.
• Group 5 - 1536 bit — The highest strength key and the most secure authentication group. It needs more time to compute the IKE keys. It is preferred if the speed of the network is high.
Step 7. Choose the appropriate Phase 2 Encryption to encrypt the key from the Phase 2 Encryption drop-down list. AES-128, AES-192, or AES-256 are recommended. The VPN tunnel needs to use the same encryption method for both of its ends.
• NULL — No encryption is used.
• DES — Data Encryption Standard (DES) uses a 56-bit key size for data encryption. DES is outdated and should be only used if one endpoint only supports DES.
• 3DES — Triple Data Encryption Standard (3DES) is a 168 bit, simple encryption method. 3DES encrypts the data three times, which provides more security then DES.
• AES-128 — Advanced Encryption Standard (AES) is 128 bit encryption method which transforms the plain text into cipher text through 10 cycle repetitions.
• AES-192 — Advanced Encryption Standard (AES) is 192 bit encryption method which transforms the plain text into cipher text through 12 cycle repetitions. AES-192 is more secured than AES-128.
• AES-256 — Advanced Encryption Standard (AES) is 256 bit encryption method which transforms the plain text into cipher text through 14 cycle repetitions. AES-256 is the most secure encryption method.
Step 8. Choose the appropriate authentication method from the Phase 2 Authentication drop-down list. The VPN tunnel needs to use the same authentication method for both ends. SHA1 is recommended.
• MD5 — Message Digest Algorithm-5 (MD5) is a 128 bit hexadecimal hash function which provides protection to the data from malicious attack by the checksum calculation.
• SHA1 — Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
• Null — No authentication method is used.
Step 9. Enter the amount of time in seconds that the Phase 2 keys are valid and the VPN tunnel remains active in the Phase 2 SA Life Time field.
Step 10. Enter a key which is shared previously between the IKE peers to authenticate the peers in the Preshared Key field. Up to 30 hexadecimal and character can be used as the preshared key. The VPN tunnel needs to use the same preshared key for both of its ends.
Note: It is strongly recommended to frequently change the preshared key between the IKE peers so the VPN remains secured.
Step 11. (Optional) If you want to enable strength meter for the preshared key, check the Minimum Preshared Key Complexity check box. It is used for determine the strength of the pre-shared key through color bars.
• Preshared Key Strength Meter — This shows the strength of the preshared key through colored bars. Red indicates weak strength, yellow indicates acceptable strength, and green indicates strong strength.
Step 12. Click Save to save the settings.
Note: If you want to configure the options available in the Advanced section for Gateway to Gateway VPN refer to the article, Configure Advanced Settings for Gateway to Gateway VPN on RV016, RV042, RV042G, and RV082 VPN Routers. Free vlc player for mac.
Objective
Cisco Rv042 Configuration
A Virtual Private Network (VPN) is a secure connection between two endpoints. A private network, that sends data securely between these two locations or networks, is established by a VPN tunnel. A VPN tunnel connects two PCs or networks and allows data to be transmitted over the Internet as if the endpoints were within a network. VPN is a good solution for companies that have employees that have to travel or be outside of the LAN often. With VPN, these employees can have access to the LAN and use the resources available to do their job. Also, VPN can connect two or more sites, so companies with different branches can communicate with each other.
Note: The RV Wired Routers Series offers two types of VPN, Gateway to Gateway and Client to Gateway. In order for the VPN connection to work properly, the IPSec values on both sides of the connection must be the same. Furthermore, both sides of the connection must belong to different LANs. The next steps explain how to configure VPN on The RV Wired Routers Series.
For the purpose of this article, the VPN configuration will be Gateway to Gateway.
This article explains how to set up a VPN Tunnel on RV016 RV042, RV042G and RV082 VPN Routers.
Applicable Devices
• RV016
• RV042
• RV042G
• RV082
Software Version
• v4.2.1.02
VPN Setup
Step 1. Log in to the Web Configuration Utility page and choose VPN > Gateway to Gateway. The Gateway to Gateway page opens:
Note: To configure a client to gateway VPN tunnel, choose VPN > Client to Gateway.
Step 2. In the Tunnel Name field, enter the name of the VPN tunnel.
Step 3. In the Interface drop-down list, choose one of the available WAN interfaces. This is the interface that will establish the VPN tunnel with the other side.
Step 4. Under Local Group Setup, in the Local Security Gateway Type drop-down list, choose one of the Listed options:
• IP Only — Choose this option if your router is configured with an static IP address for Internet connectivity.
• IP + Domain Name (FQDN) Authentication — Choose this option if your router is configured with a static IP address and a registered domain name for Internet connectivity.
• IP + Email Address (User FQDN) Authentication — Choose this option if your router is configured with a static IP address for Internet connectivity and an email address will be use for authentication.
• Dynamic IP + Domain Name (FQDN) Authentication — Choose this option if your router is configured with a dynamic IP address and a dynamic domain name will be used for authentication.
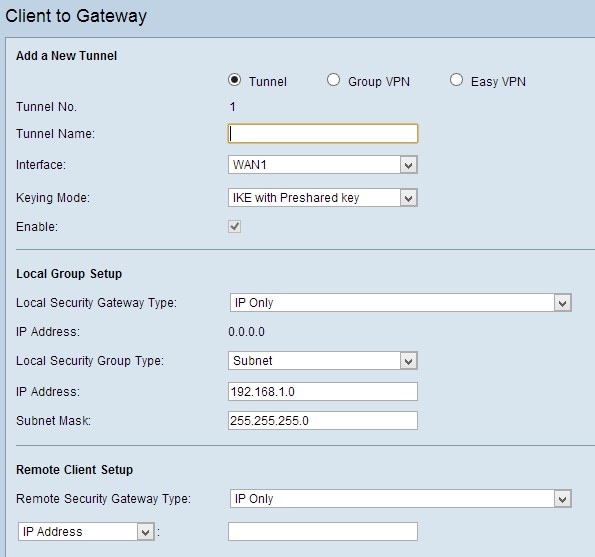
• Dynamic IP + Email Address (User FQDN) Authentication — Choose this option if your router has a dynamic IP address for Internet connectivity, but does not have a dynamic domain name for authentication and instead an email address will be used for authentication.
Step 5. Under Local Group Setup, in the Local Security Group Type drop-down list, choose one of the options:
• IP Address — This option lets you specify one device that can use this VPN tunnel. You only need to enter the IP address of the device.
• Subnet — Choose this option to allow all devices that belong to the same subnet to use the VPN tunnel. You need to enter the network IP address and its respective subnet mask.
• IP Range — Choose this option to specify a range of devices that can use the VPN tunnel. You need to enter the first IP address and the last IP address of the range of devices.
Step 6. Under Remote Group Setup, in the Remote Local Security Gateway Type drop-down list, choose one of the following:
• IP Only — Choose this option if your router is configured with an static IP address for Internet connectivity.
• IP + Domain Name (FQDN) Authentication — Choose this option if your router is configured with a static IP address and a registered domain name for Internet connectivity.
• IP + Email Address (User FQDN) Authentication — Choose this option if your router is configured with a static IP address for Internet connectivity and an email address will be use for authentication.
• Dynamic IP + Domain Name (FQDN) Authentication — Choose this option if your router is configured with a dynamic IP address and a dynamic domain name will be used for authentication.
• Dynamic IP + Email Address (User FQDN) Authentication — Choose this option if your router has a dynamic IP address for Internet connectivity, but does not have a dynamic domain name for authentication and instead an email address will be used for authentication.
Cisco Rv042 Wireless
Step 7. If you choose IP Only as the remote local security gateway type, choose one of these options from the drop-down list below:
• IP — Choose this option to enter the IP address in the adjacent field.
• IP by DNS Resolved— Choose this option if you do not know the IP address of the remote gateway, then enter the name of the other router in the adjacent field.
Step 8. Under Remote Group Setup, in the Remote Security Group Type drop-down list, choose one of the following:
• IP Address — This option lets you specify one device that can use this VPN tunnel. You only need to enter the IP address of the device.
• Subnet — Choose this option to allow all devices that belong to the same subnet to use the VPN tunnel. You need to enter the network IP address and its respective subnet mask.
• IP Range — Choose this option to specify a range of devices that can use the VPN tunnel. You need to enter the first IP address and the last IP address of the range of devices.
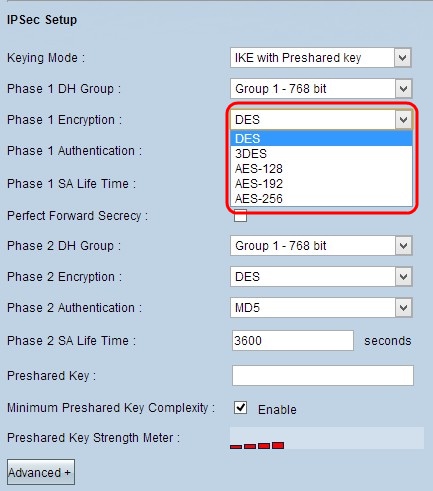
Step 9. Under IPSec Setup, in the Keying Mode drop-down list, choose one of the options:
• Manual — This option lets you configure manually the key instead of negotiating the key with the other router in the VPN connection.
• IKE with Preshared Key — Choose this option to enable the Internet Key Exchange Protocol (IKE) which sets up a security association in the VPN tunnel. IKE uses a preshared key to authenticate a remote peer.
Step 10 . DH (Diffie - Hellman) is a key exchange protocol that allows both ends of the VPN tunnel to share an encrypted key. In the Phase 1 DH Group and Phase 2 DH Group drop-down lists, choose one of the following:
• Group 1 - 768 bit — Offers faster exchange speed, but lower security. If you need the VPN session to be fast and security is not an issue, then choose this option.
• Group 2 - 1024 bit — Provides more security than Group 1, but it has more processing time. This is a more balanced option in terms of security and speed.
• Group 3 - 1536 bit — Offers less speed but more security. If you need the VPN session to be secure, and speed is not an issue, then choose this option.
Cisco Rv042 Vpn Setup Client To Gateway Router
Step 11. In the Phase 1 Encryption and Phase 2 Encryption drop-down lists, choose one of the following for encryption and decryption of the key:
• DES — Data Encryption Standard, this is a basic algorithm for encryption of data which encrypts the key in a 56 bit packet.
• 3DES — Triple Data Encryption Standard, this algorithm encrypts the key in three 64 bit packets. It is more secure than DES.
• AES-128 — Advanced Encryption Standard, this algorithm uses the same key for encryption and decryption. It offers more security than DES. Its key size is 128 bits
• AES-192 — Similar to AES-128, but its key size is 192 bits.
• AES-256 — Similar to AES-128, but its key size is 256 bits. This is the most secure encryption algorithm available.
Step 12. In the Phase 1 Authentication and Phase 2 Authentication drop-down lists, choose one of these options:

• SHA1 — This algorithm produces a hash value of 160 bits. With this value, the algorithm checks for integrity in the data exchanged, and it makes sure the data has not changed.
• MD5 — This is an algorithm design for authentication purposes. This algorithm checks the integrity of the shared information between the two ends of the VPN tunnel. It produces a hash value which is shared to authenticate the key on both ends of the VPN tunnel.
Step 13. In the Phase 1 SA Lifetime and Phase 2 SA Lifetime fields, enter the time (in seconds) the VPN tunnel is active in a phase. The default value for Phase 1 is 28800 seconds. The default value for Phase 2 is 3600 seconds.
Note: Phase 1 and Phase 2 configuration must be the same on both routers.
Step 14. (Optional) Check the Perfect Forward Secrecy check box to enable perfect forward secrecy (PFS). With PFS, IKE Phase 2 negotiation will generate new data for encryption and authentication, which enforces more security.
Step 15. In the Preshared Key, enter the key both routers will share for authentication.
Step 16. (Optional) Check the Minimum Preshared Key Complexity check box to enable the Preshared Key Strength Meter which tells you the strength of the key you create.
Step 17. (Optional) To configure more advanced encryption options, click Advanced+.
Step 18. Click Save to save your configurations.
Advanced VPN Options
If you want to add more features to your VPN setup, the RV Wired Routers Series offers advanced options. These options enhance the security features of your VPN tunnel. These options are optional, but if you set advanced options on one router, make sure to set the same options on the other router. The next section explains these options.
Step 1. In the IPSec field click on the Advanced+ button. The Advanced page opens:
Note: To configure the advanced options of a client to gateway VPN tunnel, choose VPN > Client to Gateway. Then click Advanced+.
The picture above shows an example of a configuration of the advanced options.
Step 2. Under Advanced, check the options you would like to add to your VPN setup:
• Aggressive Mode — With this option, negotiation of the key is faster, which decreases security. Check the Aggressive Mode check box if you want to improve the speed of the VPN tunnel.
• Compress (Support IP Payload Compression Protocol (IP Comp)) — With this option, the IP Comp protocol will reduce the size of the IP datagrams. Check the Compress (Support IP Payload Compression Protocol (IP Comp)) check box to enable this option
• Keep Alive — This option attempts to re-establish the VPN session if it gets dropped. Check the Keep Alive checkbox to enable this option.
Cisco Rv042 Default Ip
• AH Hash Algorithm — This option extends protection to the IP header to verify the integrity of the entire packet. Either MD5 or SHA1 can be used for this purpose. Check the AH Hash Algorithm check box and from the drop-down list, choose either MD5 or SHA1, to enable authentication of the entire packet.
• NetBIOS Broadcast — This is a Windows protocol that gives information about the different devices plugged in a LAN, such as printers, computers, and file servers. Normally, VPN doesn't transmit this information. Check the NetBIOS Broadcast check box to send these information across the VPN tunnel.
• NAT Traversal — Network Address Translation enables users in a private LAN to access Internet resources with the use of a public IP address as the source address. If your router is behind a NAT gateway, check the NAT Traversal check box.
• Dead Peer Detection Interval — Check the Dead Peer Detection Interval check box and enter (in seconds) the interval before the router sends another packets to check the connectivity of the VPN tunnel.
Cisco Rv042 Vpn Setup Client To Gateway Server
Step 3. Click Save to save your configurations.




